Continuous disclosure obligations under the Corporations Act and the ASX Listing Rules in Australia require a listed company to immediately disclose market sensitive information to the ASX. A cyber crisis or other significant data breach is likely to be “market sensitive” and require disclosure. But determining timing for disclosure, and what to disclose, in the midst of a cyber incident is not always straightforward.
In the early stages of a cyber incident, having a clear and complete understanding of the nature and extent of the incident, and its impact on the company, can be challenging. It is also likely to change on a daily (or sometimes hourly) basis as the incident unfolds. For listed companies, this challenge is particularly acute as the company attempts to juggle its continuous disclosure and other regulatory obligations with multiple other workstreams involved in responding to the incident, including forensic investigations, and communication with customers, staff, regulators, insurers and other external stakeholders.
To help listed companies, the ASX has updated Guidance Note 8 to the ASX Listing Rules to provide an example of how to apply the continuous disclosure obligations during a cyber incident, including how and when to use trading halts to manage disclosure obligations. Coming into effect on 27 May 2024, the updated version of Guidance Note 8, whilst not legally binding, is instructive as to how the ASX will interpret and apply the ASX Listing Rules and so it is generally advisable for listed companies to follow the guidance.
Continuous disclosure regime
Under ASX Listing Rule 3.1, once a listed company becomes aware of any information that a reasonable person would expect to have a material effect on the price or value of the company’s securities, it must immediately disclose this information. The resulting ASX announcement must be carefully prepared to ensure it is accurate, complete and not misleading. In the context of a complex and unfolding cyber incident, this is no easy task.
As well as being a breach of the Listing Rules, a failure to comply with Listing Rule 3.1 may also contravene s674 of the Corporations Act and give rise to serious legal consequences for the company, its officers and directors. There is also the associated risk of regulator action, class actions and brand or reputational damage.
The ASX may also step in and require the company to make an announcement, for example, where the ASX considers there is or is likely to be a false market in the company’s securities (for example, as a result of commentary in the media about the cyber incident). In our experience, the company is likely to receive an initial “please explain” from the ASX and that an announcement about the incident, if the ASX considers required, is expected on the same or next trading day. ASX may require the entity to request a trading halt while such announcement is prepared.
Exception to the disclosure obligation Listing Rule 3.1A
The exception to the obligation to disclose “market sensitive” information is found in Listing Rule 3.1A. In the context of a cyber incident, for as long as all three of the following requirements in Listing Rule 3.1A apply (and it must be all three), disclosure about the cyber incident is normally not required:
| Requirements of Listing Rule 3.1A | |
| Requirement 1 | One or more of the following situations applies:
|
| Requirement 2 | The information is confidential and ASX has not formed the view that the information has ceased to be confidential. |
| Requirement 3 | A reasonable person would not expect the information to be disclosed. |
It is important to remember that all three requirements of the exception must be met in order to rely on Listing Rule 3.1A.
For example, at the point of notifying affected individuals, the cyber incident ceases to be confidential. The company can therefore not rely on the Listing Rule 3.1A exception. The company would need to determine whether a reasonable person would expect the incident to have a material effect on the price or value of the company’s shares. If so, disclosure would be required. Accordingly, guidance from the ASX is that at the time of notifying individuals, “it would be prudent for the [the company] to first release a market announcement to ensure it complies with its Listing Rule 3.1 obligations.”
It is also important to remember that the exception in Listing Rule 3.1A will cease to apply in circumstances where the company has been issued a “price query” by ASX, or is required to issue a cleansing notice under s708A(5) of the Corporations Act. Although both of those scenarios may be entirely unrelated to the cyber incident, if the company considers the cyber incident to be price sensitive information, it must be disclosed at the time of responding to the price query or issuing the cleansing notice (as applicable).
What would a reasonable person expect to be disclosed?
The updated ASX Guidance Note 8 provides a worked example of applying Listing Rule 3.1 and the exception in Listing Rule 3.1A to a cyber incident. The example selected by the ASX follows a common sequence of events during an unfolding ransomware and extortion attack on a company.
A summary of the example and the ASX’s notes as to when disclosure would normally be required is set out below.
However, a company’s disclosure obligations will always turn on the facts; the company will need to carefully and closely keep the facts of the incident under review, as well as proactively prepared announcements, to ensure it continues to meet its obligations under Listing Rule 3.1 as the incident evolves and further information comes to light.
ASX Guidance Note 8 – worked cyber incident example
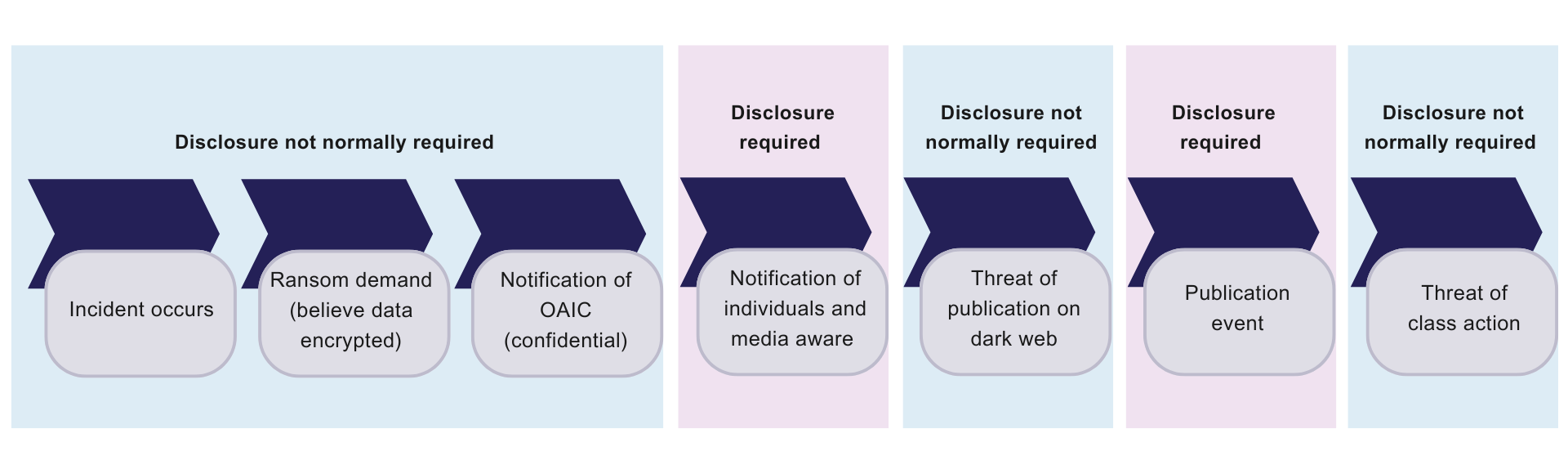
Ultimately, it is a judgement call for the company (and its Board) as to whether it is required to disclose the incident to the market through an ASX announcement and the timing for doing so. Depending on the nature of the incident and the certainty of information known to the company, this may need to occur before the company is required to notify relevant regulators and affected individuals under applicable laws, including the Privacy Act, and before the company has finalised its forensic investigations. From a strategic communications perspective, the overlay of the continuous disclosure regime can dramatically alter the way in which a company would otherwise handle its external communications during an incident, both in terms of timing and content.
Trading halts during a cyber incident
A common issue for listed companies during a cyber incident is whether or not (and when) to apply for a trading halt.
At the point during the incident response at which the company determines disclosure is required under the Listing Rules, but the company is not in a position to disclose information about the cyber incident with sufficient certainty, the company may request a trading halt.
It is the ASX’s decision whether or not a trading halt is granted and for how long. In circumstances of a cyber incident or other data breach, the ASX has confirmed in updated Guidance Note 8 that:
- The trading halt will never be granted for more than two trading days.
- It may be appropriate, in some limited circumstances, for the company to apply to go into voluntary suspension.
The ASX “strongly encourages” listed companies to engage with it as early as possible if they may need a trading halt or voluntary suspension.
What to include in the ASX announcement
Once a listed entity determines the incident is market sensitive, and all three requirements of the exception under Listing Rule 3.1A are no longer met, the listed company must immediately make an announcement.
ASX announcement must be carefully prepared to ensure they are accurate, complete and not misleading. In the context of a complex and unfolding cyber incident, this is no easy task.
Guidance from the ASX with respect to an announcement in the relatively early stages of a cyber incident (where disclosure is required) is that it would address the following:
- a description of what has occurred
- the material facts the listed company knows about the incident
- any material impact on the listed company’s operations or financial position that the company is aware of at that time
- the action the company is taking in response to the breach
- when the company expects to be in a position to update the market
As is always the case, it will be important for the company to carefully review its announcement to ensure it is factually correct and not misleading (including by omission) and does not result in a waiver of legal professional privilege.
The content of the announcement should also be considered as part of the company’s regulatory notifications that may have been or need to be made, including to the Office of the Australian Information Commissioner (OAIC) and the Australian Securities and Investments Commission (ASIC) to ensure consistency (although the content will not be the same). It will also generally be appropriate for the company to consider the timing and content of communications to its broader stakeholder groups, particularly staff.
Into the breach
With increasing regulator and community focus and heightened expectations on cyber incident response and governance, executives and directors of listed companies should understand and plan for how they will meet continuous disclosure obligations in the context of a cyber incident. This plan should be developed taking into account updated Guidance Note 8 and regularly tested, including the role of the board in key decision-making and the circumstances in which the company would go into a trading halt.
A listed company’s disclosure obligations will always turn on the facts; the company will need to carefully and closely keep the facts of the incident under review, as well as proactively prepare announcements, to ensure it continues to meet its obligations under Listing Rule 3.1 as the incident evolves and further information comes to light.
What to do if you are at risk?
If you need assistance navigating the complexities of continuous disclosure obligations during a cyber incident, our team of experts is here to help. Contact us today to ensure your company remains compliant and well-prepared to handle any cyber crisis effectively.
For more information reach out to Sophie Bradshaw, Brett Heading and Deanna Carpenter.


